Group Policy Objects (GPO) method of Secure Boot for Windows devices with IT-managed updates
Applies To
Original Published Date: October 30, 2025
KB ID: 5068198
|
This article has guidance for:
Note: If you are an individual who owns a personal Windows device, please see the article Windows devices for home users, businesses, and schools with Microsoft-managed updates. |
|
Availability of this support
|
|
Change Date |
Change Description |
|---|---|
|
February 20, 2026 |
|
|
November 11, 2025 |
|
|
November 26, 2025 |
|
In this article:
Introduction
This document describes the support for deploying, managing, and monitoring the Secure Boot certificate updates using the Secure Boot Group Policy object. The settings consist of:
-
The ability to trigger deployment on a device
-
A setting to opt in/opt out of high-confidence buckets
-
A setting to opt in/opt out of Microsoft managing updates
Note: Administrative Templates (.admx) and Group Policy will need to be downloaded from Official Microsoft site. Refer to: Resources.
Group Policy Object (GPO) configuration method
This method offers a straightforward Secure Boot Group Policy setting that domain administrators can set to deploy Secure Boot updates to all domain-joined Windows clients and servers. In addition, two Secure Boot assists can be managed with opt in/opt out settings.
To get the updates that include the policy for deploying Secure Boot certificate updates see the Resources section below.
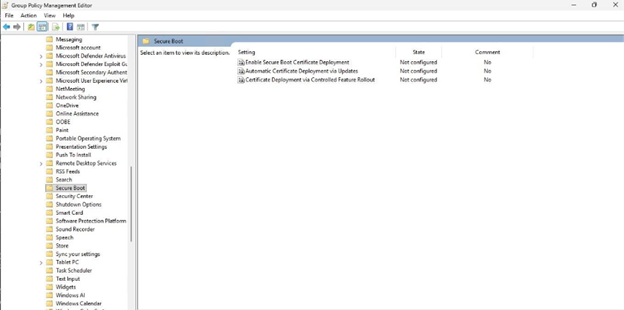
This policy can be found under the following path in the Group Policy UI:
Computer Configuration->Administrative Templates->Windows Components->Secure Boot
Important: Secure Boot updates depend on device firmware, and some devices may experience compatibility issues. To ensure a safe rollout:
-
Validate the update policy on at least one representative device for each device type in your organization.
-
Confirm that Secure Boot certificates are successfully applied to the UEFI DB and KEK. For detailed steps, visit Secure Boot Certificate updates: Guidance for IT professionals and organizations.
-
After validation, group devices by bucket hash and apply the policy to those devices for a controlled rollout.
Available Configuration Settings
The three settings available for Secure Boot certificate deployment are described here. These settings correspond to the registry keys described in Registry key updates for Secure Boot: Windows devices with IT-managed updates.
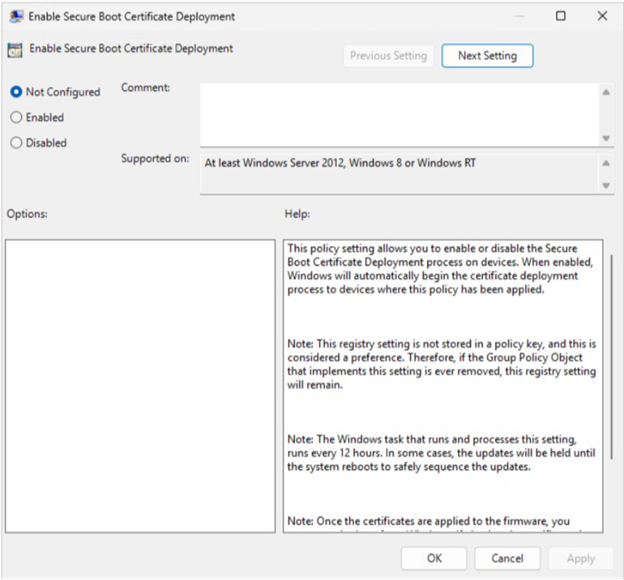
Enable Secure Boot Certificate Deployment
Group Policy setting name: Enable Secure Boot Certificate Deployment
Description: This policy controls whether Windows initiates the Secure Boot certificate deployment process on devices.
-
Enabled: Windows automatically begins deploying updated Secure Boot certificates once the Secure Boot task runs.
-
Disabled: Windows does not deploy certificates automatically.
-
Not Configured: Default behavior applies (no automatic deployment).
Notes:
-
The task that processes this setting runs every 12 hours. Some updates may require a restart to complete safely.
-
Once certificates are applied to firmware, they cannot be removed from Windows. Clearing certificates must be done through the firmware interface.
-
This setting is considered a preference; if the GPO is removed, the registry value remains.
-
Corresponds to the registry key AvailableUpdates.
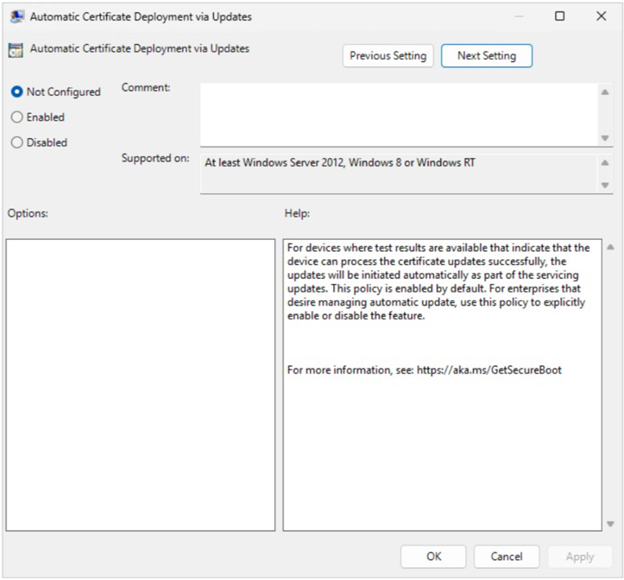
Automatic Certificate Deployment via Updates
Group Policy setting name: Automatic Certificate Deployment via Updates
Description: This policy controls whether Secure Boot certificate updates are applied automatically through Windows monthly security and non-security updates. Devices that Microsoft has validated as capable of processing Secure Boot variable updates will receive these updates as part of cumulative servicing and apply them automatically.
Note: Enabling this policy disables Automatic Certificate Deployment via Updates. This is equivalent to setting the HighConfidenceOptOut registry key to 1. Disabling this policy opts in to Automatic Certificate Deployment via Updates, which is equivalent to setting HighConfidenceOptOut to 0.
-
Enabled: Automatic deployment is blocked; updates must be managed manually.
-
Disabled: Devices with validated update results will receive certificate updates automatically during servicing.
-
Not Configured: Automatic deployment occurs by default.
Notes:
-
Intended devices confirmed to process updates successfully.
-
Configure this policy to opt for automatic deployment.
-
Corresponds to the registry key HighConfidenceOptOut.
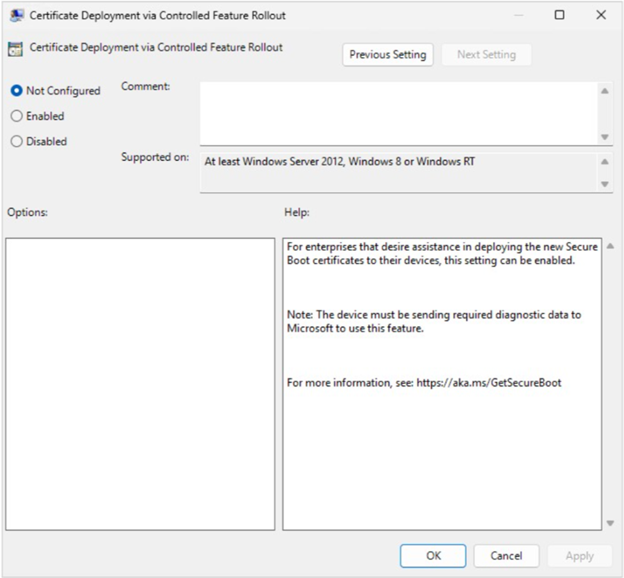
Certificate Deployment via Controlled Feature Rollout
Group Policy setting name: Certificate Deployment via Controlled Feature Rollout
Description: This policy allows enterprises to participate in a Controlled Feature rollout of Secure Boot certificate update managed by Microsoft.
-
Enabled: Microsoft assists with deploying certificates to devices enrolled in the rollout.
-
Disabled or Not Configured: No participation in controlled rollout.
Requirements:
-
Device must send required diagnostic data to Microsoft. For details, see Configure Windows diagnostic data in your organization - Windows Privacy | Microsoft Learn.
-
Corresponds to the registry key MicrosoftUpdateManagedOptIn.
Resources
See also Registry key updates for Secure Boot: Windows devices with IT-managed updates for details on the UEFICA2023Status and UEFICA2023Error registry keys for monitoring device results.
See Secure Boot DB and DBX variable update events for events useful in understanding the status of devices, device attributes, and device bucket IDs. Pay special attention to events 1801 and 1808 described on the events page.
For the Group Policy MSIs and the GP Settings Reference Spreadsheet, use the links below or ensure that the administrative templates you use are published on or after the dates listed in the table.
|
Platform |
Published MSI |
Published GP Settings Reference Spreadsheet |
|---|---|---|
|
Client Note: The Administrative Templates (.admx) are OS agnostic and work across ALL supported OS'es. |
Published: 10/27/2025 |
Published: 10/2/2025 |
|
Server Note: The Administrative Templates (.admx) are OS agnostic and work across ALL supported OS'es. |
Published: 10/27/2025 |
Published: 10/27/2025 |