Windows devices for businesses and organizations with IT-managed updates
Applies To
Original publish date: June 26, 2025
KB ID: 5062713
|
This article has guidance for:
Note If you are an individual who owns a personal Windows device, please go to the article Windows devices for home users, businesses, and schools with Microsoft-managed updates. |
Overview
The configuration of certificates provided by Microsoft as part of the Secure Boot infrastructure has remained the same since Windows 8. These certificates are stored in the Signature Database (DB) and Key Enrollment Key (KEK) (also known as Key Exchange Key) variables in the firmware. Microsoft has provided the same three certificates across the original equipment manufacturer (OEM) ecosystem to include in the device's firmware. These certificates support Secure Boot in Windows and are also used by third-party operating systems (OS), which include the following Microsoft-provided certificates:
-
Microsoft Corporation KEK CA 2011
-
Microsoft Windows Production PCA 2011
-
Microsoft Corporation UEFI CA 2011
Important
All three Microsoft-provided certificates are set to expire beginning in June 2026. So, in collaboration with our ecosystem partners, Microsoft is rolling out new certificates that will help ensure Secure Boot security and continuity for the future. Once these 2011 certificates expire, security updates for boot components will no longer be possible, compromising boot security and putting affected Windows devices at risk. To maintain Secure Boot functionality, all Windows devices must be updated to use the 2023 certificates before the 2011 certificates expire.
Note: This article refers to “certificates” and “CA” (Certificate Authority) interchangeably.
Windows Secure Boot certificates expiring in 2026
Windows devices manufactured since 2012 may have expiring versions of certificates which must be updated.
Terminology
-
KEK: Key Enrollment Key
-
CA: Certificate Authority
-
DB: Secure Boot Signature Database
-
DBX: Secure Boot Revoked Signature Database
|
Expiring Certificate |
Expiration date |
New Certificate |
Storing location |
Purpose |
|
Microsoft Corporation KEK CA 2011 |
June 2026 |
Microsoft Corporation KEK CA 2023 |
Stored in KEK |
Signs updates to DB and DBX. |
|
Microsoft Windows Production PCA 2011 |
Oct 2026 |
Windows UEFI CA 2023 |
Stored in DB |
Used for signing the Windows boot loader. |
|
Microsoft UEFI CA 2011* |
June 2026 |
Microsoft UEFI CA 2023 |
Stored in DB |
Signs third-party boot loaders and EFI applications. |
|
Microsoft UEFI CA 2011* |
June 2026 |
Microsoft Option ROM CA 2023 |
Stored in DB |
Signs third-party option ROMs |
*During renewal of the Microsoft Corporation UEFI CA 2011 certificate, two certificates separate boot loader signing from option ROM signing. This allows finer control over system trust. For example, systems that need to trust option ROMs can add the Microsoft Option ROM UEFI CA 2023 without adding trust for third-party boot loaders.
Microsoft has issued updated certificates to ensure continuity of Secure Boot protection on Windows devices. Microsoft will manage the update process for these new certificates on a significant portion of Windows devices and will offer detailed guidance for organizations that manages their own device’s updates.
Scope for Enterprise and IT professional managed systems
This article is targeted at organizations that do not share diagnostic data with Microsoft and have dedicated IT professionals who manage updates to their environment. Currently, there is insufficient information for Microsoft to fully support rolling out the Secure Boot certificates on these devices, especially those with diagnostic data disabled.
Enterprises and IT professional have the choice to get such systems to be Microsoft-managed systems, in which case Microsoft updates the Secure Boot certificates. However, we realize that this is not a feasible option for a variety of devices such as air-gapped devices in government, manufacturing, and so forth. In these cases, Microsoft support will be limited to recommending known steps or methods for deploying these updates as well as sharing data gathered from our rollout stream. This will be provided through updated versions of this article.
What solutions can Enterprise or IT professional managed devices expect?
Option 1: Fully automated (only for Microsoft managed devices)
By choosing this option, your devices will automatically receive the latest Secure Boot updates, helping keep your devices safe and secure. To enable this, you will need to participate in and allow Microsoft to collect Universal Telemetry Client (UTC) diagnostic data from your devices. This step ensures your devices are enrolled in the Microsoft managed program and will receive all updates seamlessly as part of our standard rollout.
Rollout Strategy
For Windows devices that rely on Microsoft to apply the Secure Boot certificate updates to their device's, we utilize a very meticulous rollout strategy. We group systems with similar hardware and firmware profiles (based on Windows diagnostic data and OEM feedback), then gradually release updates to each group. Throughout this process, we closely monitor diagnostic feedback to ensure that everything runs smoothly. If any issues are detected in a group, we pause and address them before resuming rollout to that group.
Call to action
To be included in the Microsoft managed deployment, we suggest enabling Windows diagnostic data. With this, we can identify and target eligible devices for Secure Boot certificate updates.
Why does diagnostic data matter?
The Microsoft managed rollout strategy relies heavily on the diagnostic data we receive from the systems as we have included data signals that inform us of the state of the devices in reaction to installing the new Secure Boot certificates. This way, we can quickly identify issues in our rollout and proactively pause rollout to devices with similar hardware configurations to minimize the impact of the issue.
Enabling diagnostic data ensures your devices are visible. It will move your devices into the Microsoft managed stream for automated targeting and delivery of these updates.
Notes
-
Organizations that prefer not to enable diagnostic data will remain in full control and will receive future tools and guidance to manage the update process independently.
-
For the solutions highlighted here, you have the ultimate responsibility to monitor the progress of the updates to all devices in your environment and may have to use more than one solution to achieve full adoption.
To participate in the Microsoft managed rollout, please follow these steps:
-
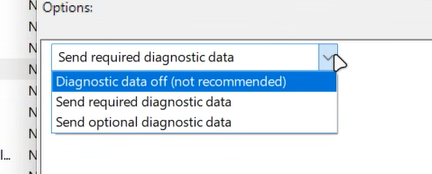
Follow the Configure Windows diagnostic data in your organization and set the data setting to allow required diagnostic data. In other words, do not set to Disabled and do not set turn off diagnostic data. Any setting that provides more than required diagnostic data will also work.
-
Choose to participate in Microsoft managed updates for Secure Boot by setting the following registry key:
Registry location
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Secureboot
Key name
MicrosoftUpdateManagedOptIn
Key type
DWORD
DWORD value
-
0 or key does not exist
-
0x5944 – Secure Boot opt-in
Comments
We recommend setting this key to 0x5944 to indicate that all certificates should be updated in a manner that preserves the security profile of the existing device and updates the boot manager to the one signed by the Windows UEFI CA 2023 certificate.
Note This registry key will be enabled in a future update.
-
Note Support for the Microsoft managed rollout is only available for Windows 11 and Windows 10 client versions. After October 14, 2025, Windows 10, version 22H2 with extended security updates (ESU) will be included.
Option 2: Self-service or partially automated solutions
Microsoft is evaluating guidance for partially automated solutions to assist enterprise and IT professional managed systems. Please note that these are self-service options that an enterprise or IT professionals can choose to apply as per their specific situation and usage model. More information will be provided when this option is available.
|
As Microsoft has limited visibility (or diagnostic data) for Enterprise and IT professional managed devices overall, please fill out the Microsoft survey form. This will help us gain a better understanding of your environment and its requirements so we can support you through the Secure Boot certificate rollout transition before June 2026. |
 |
Manual DB/KEK update steps
For instructions on how to manually apply the Secure Boot DB updates, see Updating Microsoft Secure Boot keys. Additionally, for details on Microsoft recommended Secure Boot object configuration, see Microsoft Secure Boot objects GitHub Repo as it is the official spot for all Secure Boot object content.
IMPORTANT
The Secure Boot certificate updates offered by Microsoft through Windows Update (WU) are applied to the active Secure Boot certificate variables; these updates are not persistent. If the Secure Boot state on a device is toggled from On to Off, the updates might be removed, as the active variables are reset. Consequently, even if Secure Boot is later re-enabled, the device will no longer retain the 2023 Secure Boot certificate updates that were previously installed through WU. This is because the updates from Microsoft are to the active variables of the Secure Boot certificates and not its default variables.
To address this, Microsoft is working with OEM partners to deliver firmware updates to the default variables of these Secure Boot certificates. This way even when Secure Boot state is toggled off and then back on, the systems active variables will inherit the updated contents from the default variables, thereby retaining the 2023 Secure Boot certificate updates.
|
Change date |
Change description |
|
July 8, 2025 |
|
|
July 2, 2025 |
|